Penetration Testing Services
POWERED BY
TEMIKA CYBER
Our certified testers will combine the manual and automated tools to do attack simulation and examine your system to uncover hidden vulnerabilities that could expose your organization to potential breaches. After that, we will provide reports that highlight identified vulnerabilities, along with their severity levels and recommended remediation strategies.
Defining the scope and objectives of testing such as target systems, applications, and network infrastructure.
Simulate real-world attacks through automated and manual tools to identify weaknesses and potential entry points for attackers.
Expose identified vulnerabilities, their severity, and potential impacts along with recommendations for remediation to solve it.



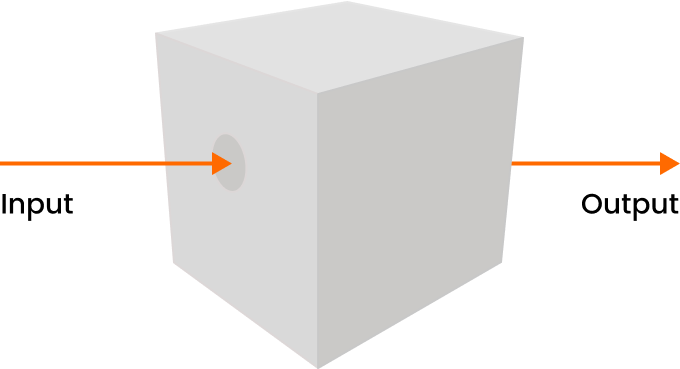
Testing is given complete information by the target, so that it can find out all the information to be tested including the internal system or source code.
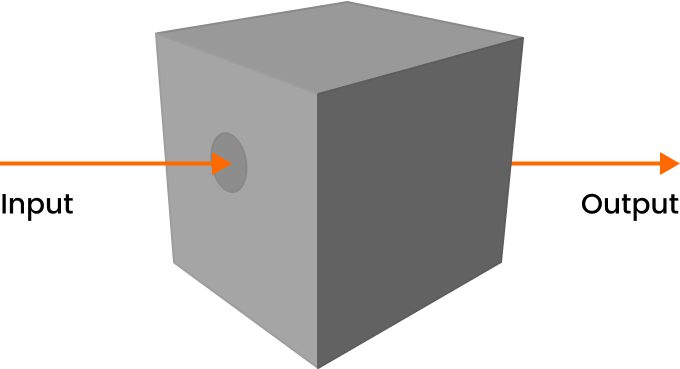
Testing is done with partial knowledge of the target to be tested such as using an account for testing.
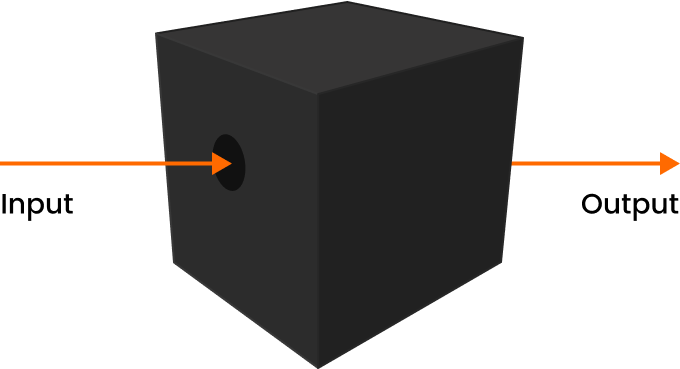
The test is not provided with information by the target, can only test the target from the outside.
Common targets for penetration testing include
Mobile Application (Android & iOS)
Internet of Things (IoT)
Web Application
Thick Client / Desktop application
Network Infrastructure
(Wireless, Active Directory, VPN endpoint, email, etc)
The penetration testing method following industry standards
NISTSP800-115
Open Source Security Testing Methodology Manual (OSSTMM)
Open Web Application Security Project (OWASP)
Penetration Testing Execution Standard (PTES)
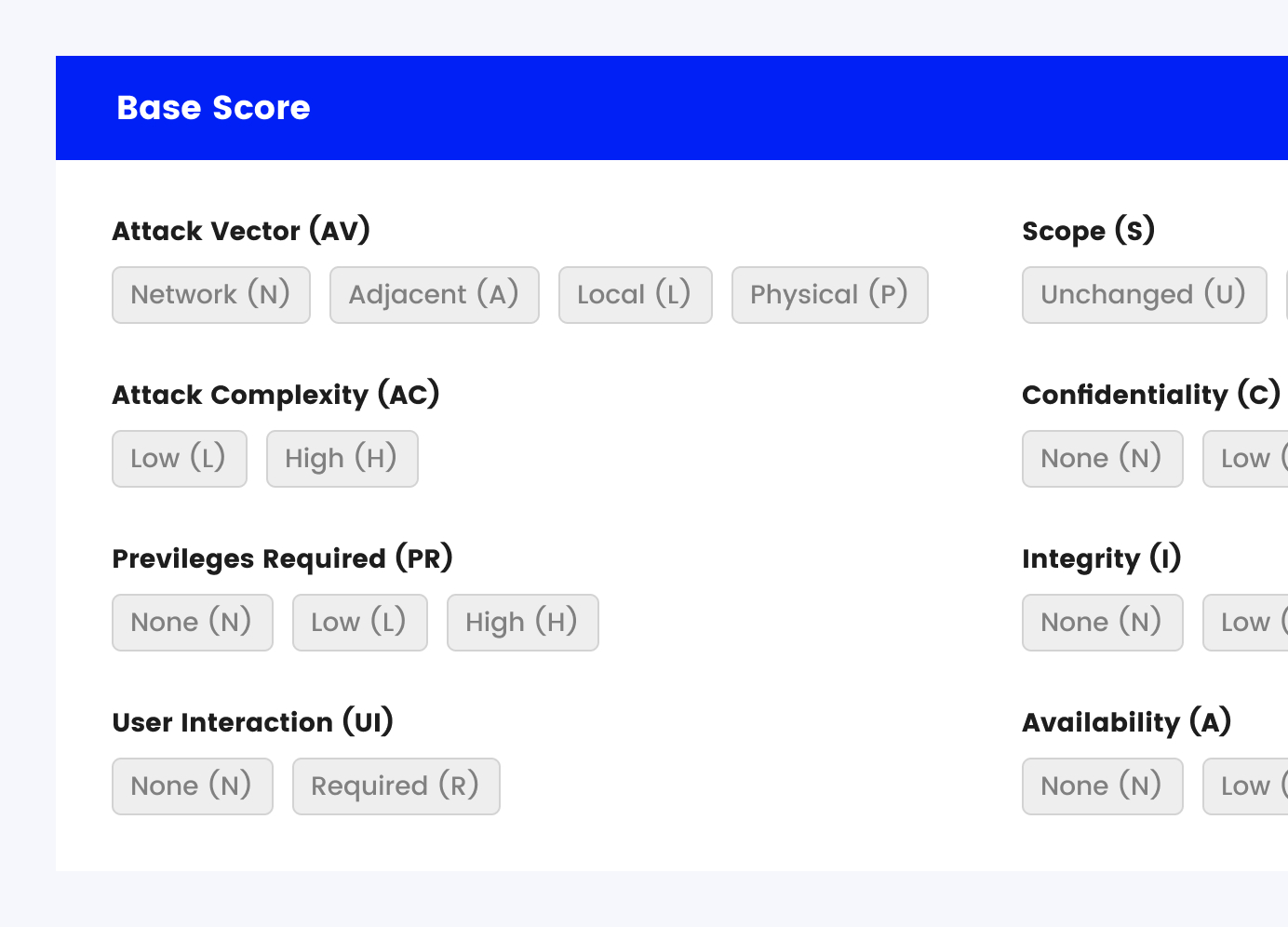
Hover over metric group names, metric names and metric values for a summary of the information in the official CVSS v3.1 Specification Document. The Specification is available in the list of links on the left, along with a User Guide providing additional scoring guidance, an Examples document of scored vulnerabilities, and notes on using this calculator (including its design and an XML representation for CVSS v3.1).