Security Operation Center
POWERED BY
TEMIKA CYBER
In delivering SOC/MDR 24/7 services we proactively secure your business data with real-time monitoring to respond threats immediately. Our experts will set the role to defend your business from hackers by analyzing your network, systems, and data, ensuring rapid detection and response to potential security incidents. With real-time threat monitoring, we’ll give you the coverage you need for your digital assets.
24/7 monitoring your infrastructure, applications, network to detect and respond to security incidents in real-time.
By implementing proactive defense measures, such as robust access controls, network segmentation, and intrusion prevention systems, we prevent upcoming attacks.
Initiate incident response protocols to mitigate the threat and develop effective remediation strategies for security.
A structured process that combines monitoring, threat detection, incident analysis, and rapid response—using expert tools, automation, and intelligence to protect systems continuously.
We defining quality standards and objectives for Security Operation Center (SOC) services, including determining the criteria for measuring performance and effectiveness.
We ensuring that the planned quality standards are met throughout the delivery of SOC services. This involves monitoring and evaluating processes to identify and address any deviations or deficiencies.
We inspecting, testing, and monitoring SOC services to ensure that they meet the predefined quality standards. This involves detecting and correcting errors or defects to maintain the desired level of quality in the delivered services.
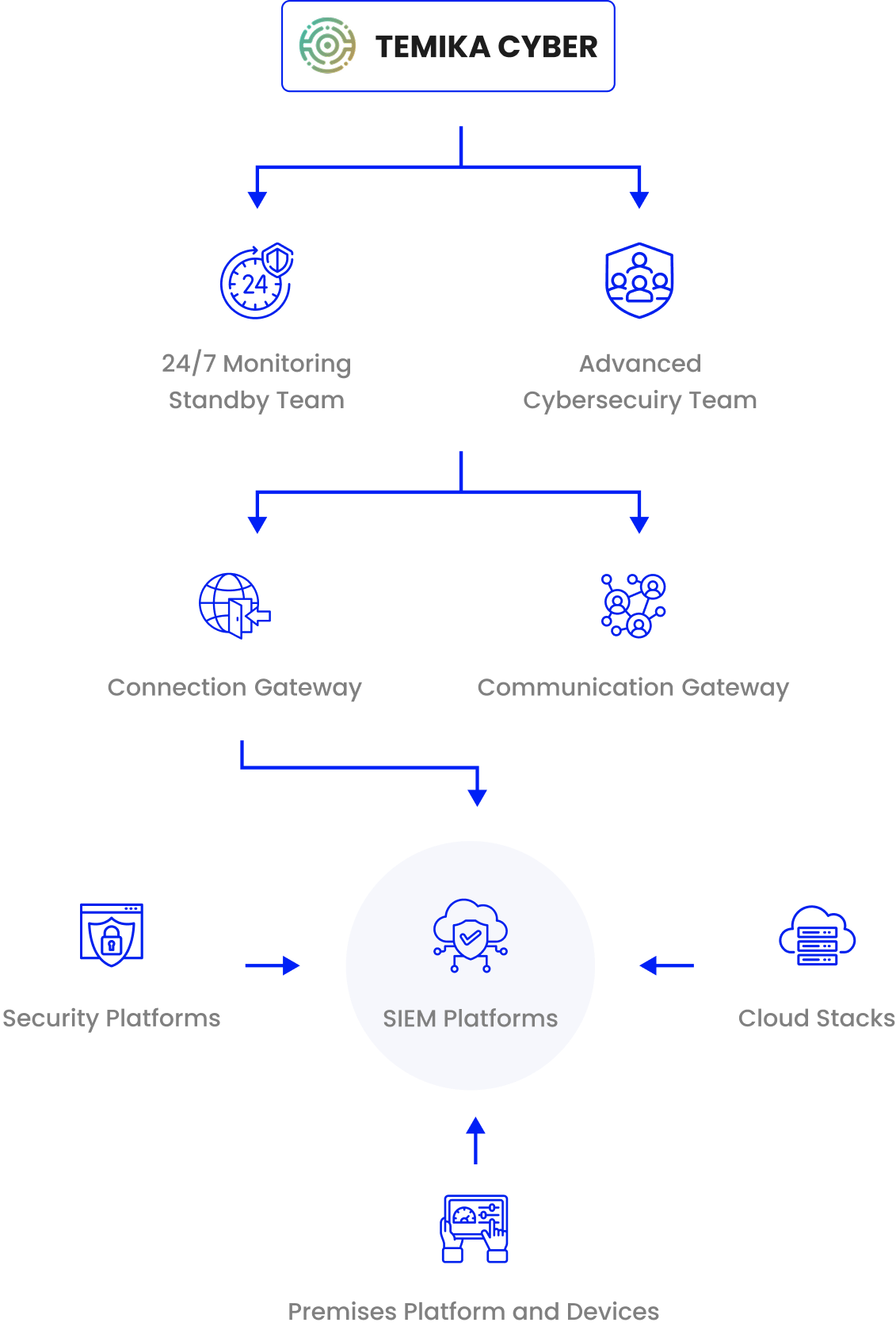
Temikaa team will always connected to customer IT Premises through a secured VPN/Tunneling connection
SOC team remotely secured access into monitoring platform All customer’s data integrated and ingestion to SIEM log management
A structured process that combines monitoring, threat detection, incident analysis, and rapid response—using expert tools, automation, and intelligence to protect systems continuously.
Providing strategic direction within the internal organization to ensure service quality and delivery alignment, preparing service frameworks, and evaluating service development and improvement in quality.
Managing service operations, overseeing teams and performance to ensure service level agreement (SLA) success, and ensuring services are delivered effectively and accurately.
The team responsible for service delivery and directly interacting in the service delivery process to customers.

| Level | Definition | Parameter | First Response (Alert With initial analysis) | First Response (Alert With initial analysis) |
|---|---|---|---|---|
| Severity 1 | Critical Compromise Major service distruption of publicly displayed attack |
|
|
1 Hour |
| Severity 2 | Serious Impact or Compromise Attack affect in multiple systems |
|
|
3 Hours |
| Severity 3 | Intermittent Incident or alerts, but not critical |
|
60 minutes initial analysis | 6 Hours |
| Severity 4 | Informational, no security impact |
|
120 minutes initial analysis | 12 Hours |
Instant report that sent near real time once security alert occures
Instant report that summarized last and followed up security alert report
Summary executive report for last week monitoring activities
Monthly basis report for monitoring activities including all security analysis, ticket tracking and so on along last month period
Managed SOC Services
Kick Off, Project Administration, and team onboarding to define communication strategy and platform onboarding
Full 12 months SOC 24/7 operational
SOC 24x7 Team; SOC 8x5 Team; 8x5 Shared SOC Representative
XYZ Corporation is a large financial services company with multiple branches and a significant online presence. As the company grew, it faced increasing cybersecurity threats and struggled to effectively manage and respond to security incidents. Recognizing the need for enhanced security capabilities, XYZ Corporation decided to outsource its security operations to a trusted Managed Security Service Provider (MSSP) with a dedicated SOC/MDR.
XYZ Corporation partnered with an MSSP specializing in SOC Managed Services to address their security challenges. The MSSP implemented the following solutions:
24/7 Security Monitoring
Incident Response & Threat Intelligence
Security Device Management
Advanced Threat Hunting
Compliance and Reporting
Security Awareness
The organization is building a SOC to strengthen cybersecurity, focusing on structure, maturity, and key initiatives.
We assess the SOC's current maturity, design its framework, define team, processes, and tech needs, and align it with the organization's overall security systems, including CSIRT, DRP, and BCM.
SOC Blueprint (Framework, Governance, Team Structure, Technology, and initiatives references)
The organization is planning strategically, with a focus on cybersecurity. A key challenge is building a functional SOC that aligns with its needs in terms of governance, structure, and technology.
We conduct interviews and review documents to assess SOC readiness, help develop process governance, and provide guidance on team structure and technology for effective SOC operations.
The organization is implementing a Security Operations Center (SOC) and faces the challenge of developing process flows and operational procedures that support both internal teams and external managed service providers.
We review the organization's current cybersecurity functions and systems, develop a process framework, define SOC team roles, and provide guidance for implementing an on-premise SOC within the organization.